Risk management strategies are the practical steps businesses take to spot risks, reduce their impact, and keep operations running smoothly. In this guide, you’ll see what an example of a risk management strategy is, and how to put a plan into action with clear examples and proven methods.
TL;DR
📝 Run a fast risk assessment, then prioritize with a simple matrix.
📋 Stand up a risk register with owners and next actions.
⚖️ Choose the proper treatment: avoid, mitigate, transfer, or accept.
📊 Track KRIs, review monthly, and update playbooks after incidents.
🚀 Start this week: one high-impact risk, one owner, one control.
Why Risk Management Strategies Matter
You don’t need a 50-page policy to start reducing risk this week. In the next 10 minutes, you’ll see exactly how to score risks, pick the right response, and keep your team moving without drama.
An example of a risk management strategy is running a structured risk assessment and applying clear mitigation strategies to reduce the likelihood or impact of major threats. In this guide, you’ll see how to design and implement your own risk management plan — with real-world examples, practical frameworks, and proven methods you can start using this week.
Every business faces uncertainty, but not all are ready for it. An example of a risk management strategy is running a structured risk assessment to spot and prioritize threats before they escalate.
By implementing the right risk management strategies, you’ll reduce the chance of financial loss, reputational harm, and operational breakdowns. In this guide, we’ll walk you through 10 practical approaches: from building a risk register to applying mitigation strategies, that help you manage various types of risks and strengthen your long-term resilience. For a complete overview of the project risk management process in projects, this guide walks you through the core steps, tools, and templates.
Why listen here?
I started my project management career in financial services, where risk management was part of every project from day one. Since then, I’ve applied it across industries that don’t always take it seriously, and the feedback has been the same: being proactive about risks has made stakeholders more confident in the recommendations and deliverables. That experience shapes the practical steps you’ll see in this article.
How to implement your risk management plan in week one
The value of a risk management plan isn’t in the document itself; it’s in the speed you implement it. In the first week, aim for practical over perfect:
- Start with your top three risks. Choose the most obvious issues you face (e.g., supplier delays, data breaches, cash flow gaps).
- Assign owners. Decide who manages each risk and make it visible. Ownership creates accountability from day one.
- Add simple controls. Quick wins, such as MFA, dual payment approval, and a backup supplier, reduce exposure immediately.
- Set a review rhythm. Meet weekly to update the risk register and track progress against the risk management steps.
By the end of week one, you’ll have a living plan in motion. It won’t be perfect, but you’ll already be cutting risk and building a culture where risk management is part of everyday decisions.
Why Risk Management Strategies and Mitigation Strategies Protect Your Business
Identification comes first. The goal isn’t a perfect list; it’s a reliable signal of what can hurt you the most, fastest. Focus on breadth first, then depth. Thorough risk identification is the backbone of effective risk management.
Key moves that consistently work:
- Run a risk assessment to pinpoint and size your biggest exposures.
- Build a clear risk register to keep everyone aligned.
- Involve stakeholders early and review the register regularly so it stays current.
If your register doesn’t change monthly, you’re not listening to your environment.
Conduct a risk assessment to spot types of risks and manage risks early
A solid risk assessment looks at internal and external factors that threaten your goals.
- Internal: process failures, outdated systems, skills gaps, compliance debt.
- External: market shifts, regulatory changes, supplier instability, and severe weather.
How to do it well:
- Bring a cross-functional team (finance, operations, legal, IT).
- Use proven tools like SWOT or PESTEL to look at the bigger picture.
- Capture both obvious and “slow-burn” risks that can snowball later.
- Document assumptions so scoring stays consistent across teams.
Prioritize common risks by likelihood and severity (practical risk management steps)
After you list risks, rank each by likelihood (1–5) and impact (1–5). Assess the likelihood with factors such as historical data, industry trends, and expert opinions. Evaluate the impact on various aspects of the business, including financial, reputational, and operational consequences.
Then:
- Plot them on a color-coded matrix (red/amber/green).
- Treat high-likelihood/high-impact first.
- Park low/low items on a watchlist.
- Assign owners and next actions for everything above the line.
Your matrix becomes the work queue for mitigation strategies and resourcing.
Build a living risk register
Your risk register is the single source of truth. For each item, include:
- A short description and the affected business area.
- Likelihood and impact scores (with date of last review).
- Current controls, gaps, and the next action.
- Named owner and due dates.
Treat it like a product backlog: update weekly, close items promptly, and surface blockers fast.
Regularly update and review the risk register within your risk management plan
Review the register at least quarterly, or monthly in fast-moving contexts.
- Validate that risks are still relevant.
- Re-score where data or context has changed.
- Add new risks from incidents, audits, or market signals.
- Communicate changes to stakeholders so decisions reflect the latest picture.
A current register is the difference between “we thought about it once” and effective risk management.
Risk Management Strategies in Practice: Scoring Risks with a Consistent Risk Response
Your goal here is consistency. Teams should score and respond to risks the same way, regardless of who’s in the room.
Evaluate the likelihood of each risk occurring (use a formal risk assessment)
Judge likelihood using:
- Internal data: incidents, outages, audit findings, and defect rates.
- External signals: industry benchmarks, tech advancements, vendor health, economic or regulatory trends.
- Expert input: line managers and specialists closest to the work.
Agree as a group on what “unlikely”, “possible”, and “likely” mean in observable terms, then apply the same scale across teams.
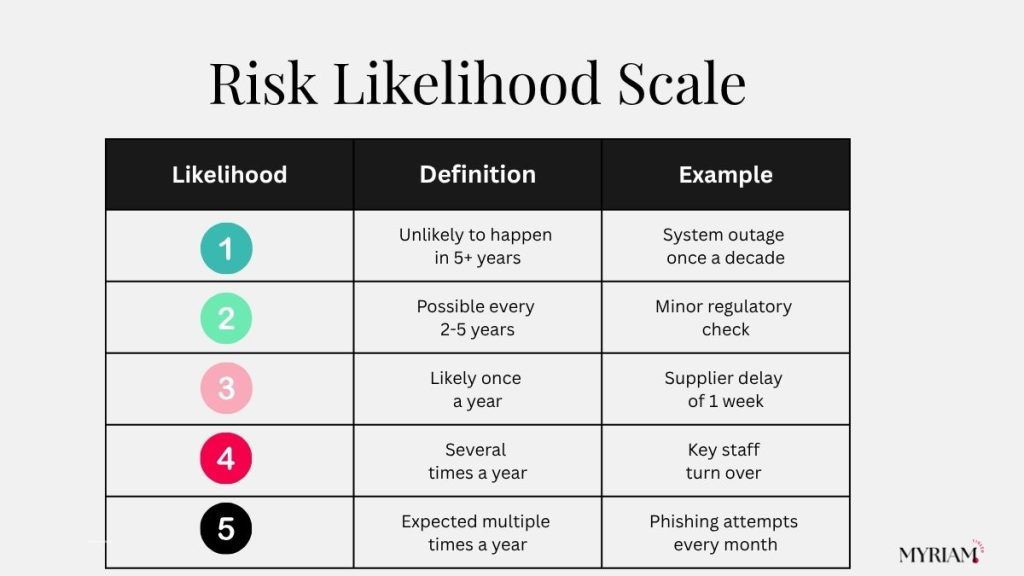
Use a probability scale that’s easy to apply
Use a 1–5 scale with plain-language definitions and examples. Keep it simple, measurable, and auditable. The simpler the scale, the more consistent the scoring.
Likelihood (1-5) | Definition | Example Trigger |
|---|---|---|
1 – Rare | Very unlikely to occur | Once every 5+ years |
2 – Unlikely | Possible but not expected | 1 incident every 2–3 years |
3 – Possible | Could happen occasionally | 1 – 2 incidents per year |
4 – Likely | Will probably happen | Quarterly incident frequency |
5 – Almost Certain | Expected to occur regularly | Monthly or more frequent |
Determine the impact of a risk (financial, operational, reputational)
Impact is the consequence if the event happens. Quantify with thresholds:
- Financial: revenue hit bands, unexpected cost ranges, penalties.
- Operational: downtime minutes/hours, backlog growth, SLA breaches.
- Reputational/compliance: customer churn markers, press risk, regulatory action.
Develop impact categories and scales aligned to your risk management plan
Impact scores mean more when they’re tied to real thresholds, not vague labels. A good practice is to map a 1–5 scale to your actual business numbers — for example:
- 1 (Low): Minimal disruption, fixed within hours.
- 3 (Medium): Moderate cost or delay, requires escalation.
- 5 (High): Direct financial hit, compliance exposure, or reputational damage.
Document these thresholds inside your risk management plan. That way, when teams debate impact, they’re all using the same yardstick. And because the scale feeds directly into your risk matrix, you get a consistent way to compare and prioritize what matters most.
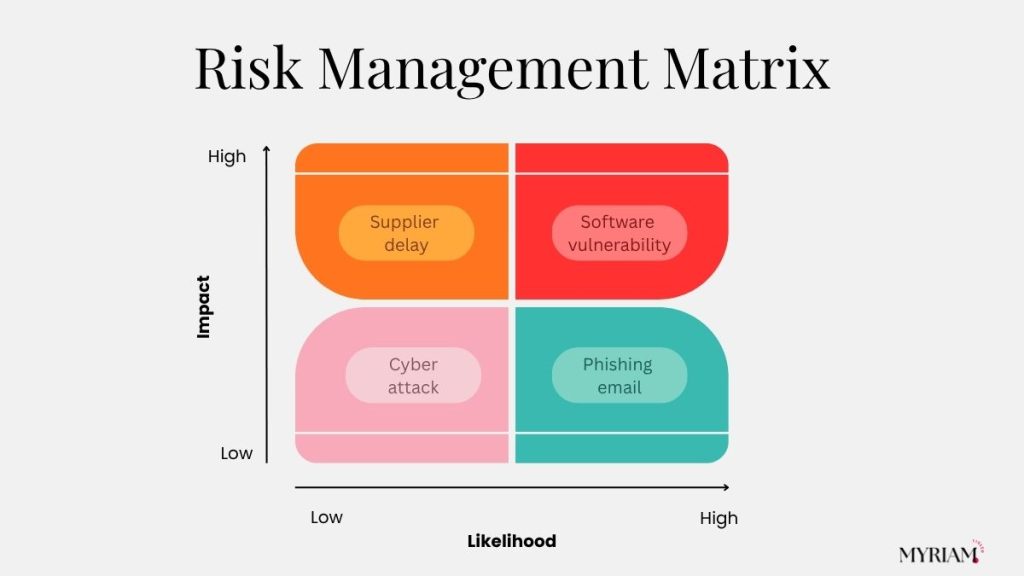
Create a risk matrix to prioritize what to treat first
Put likelihood on one axis, impact on the other, then prioritize:
- High/High: immediate action, funded mitigation, executive visibility.
- High/Low: quick and cheap controls; monitor closely.
- Low/High: contingency plans; consider insurance or contractual transfer.
- Low/Low: monitor and revisit during quarterly reviews.
Engage stakeholders to manage risk consistently
Consistency beats heroics. Bring in department heads, frontline experts, finance, legal, and key suppliers when relevant.
- Confirm risk appetite with leadership so trade-offs are explicit.
- Agree on who is accountable for each response.
- Record decisions and rationales so audits (and future hires) can follow the thread.
Define common risk categories and scoring thresholds
Common risks are the everyday issues that disrupt if ignored:
Late supplier deliveries, brief system downtime, non-critical staff turnover, and minor regulatory queries.
Set clear thresholds so no one argues about severity:
- Low: minimal disruption, fixed within a day.
- Medium: cost/delay, escalation within a week.
- High: direct financial hit, reputation, or compliance exposure.
Document this in the plan and teach it. When everyone uses the same benchmark, you manage risk faster and more fairly.
Standardize your standard risk response playbooks
Turn recurring situations into playbooks with owners, steps, and triggers. A playbook is a simple checklist: “If X happens, here’s who does what.”
Examples:
- IT outage (Medium): switch to backup, notify users, and capture post-incident notes.
- Supplier delay (High): trigger secondary supplier order, update customers, escalate in weekly risk review.
- Minor compliance query (Low): assign to legal, reply within 48 hours, log in the register.
Playbooks shrink response time, reduce guesswork, and make behavior consistent across teams.
By standardizing, you not only cut response time but also show auditors, investors, and customers that your risk management process is mature and repeatable.
Types of Risk Management Strategies #4–6: Control Risks Proactively
Develop strategies to avoid, reduce, or transfer risks. Your aim is to minimize likelihood and impact, and protect the business with smart insurance and outsourcing where it makes sense.
Context before you choose: confirm the risk appetite, treatment cost vs. exposure, and any compliance constraints.
Develop risk mitigation and risk avoidance strategies (choose the proper risk treatment)
🚫 Risk avoidance removes the exposure entirely (e.g., stop collecting a sensitive data type, or exit a volatile market). Use it when the downside can’t be justified.
🛡 Risk mitigation reduces the likelihood or impact with controls (e.g., MFA, code reviews, safety training, physical security).
Choose treatment based on the matrix score, cost-benefit analysis, and regulatory expectations.
Identify high-impact common risks and define your risk response
Focus on the risks that could meaningfully harm customers, revenue, or compliance:
- Cyber incidents and data loss
- Natural disasters and facility outages
- Supply chain disruption
- Regulatory non-compliance
For each, write a short response plan with owners, time targets, and communication steps.
Implement risk controls: modify processes or operations to manage risk
Examples that work quickly:
- Encryption at rest/in transit, principle of least privilege, vendor access reviews.
- Fire suppression and evacuation drills, as well as backup power at critical sites.
- Dual approval for payments, inventory buffers, and alternate logistics routes.
- Policy refreshers with sign-off to close compliance gaps.
🛡 Use mitigation strategies for risk reduction (keep effective risk controls simple)
Simple beats clever. Controls fail when they’re hard to follow.
- Pick the smallest control that materially reduces exposure.
- Pilot it with one team, then roll out.
- Measure before/after (incidents, downtime, cost) to prove value.
Implement controls that reduce risk and support effective risk management
Make it visible and measurable:
- Add each control to the register.
- Assign an owner and due date.
- Track impact and re-score the risk after implementation.
Invest in training and resources to manage risk consistently
People make controls work. Provide:
- Cyber awareness refreshers, practical safety briefings, crisis drills.
- Checklists and job aids at the point of work.
- Clear escalation paths when something feels off.
🔄 Risk transfer to a third party (who is responsible for developing a risk response?)
Sometimes, the most brilliant move is to move the exposure.
- Insurance: cyber, property, business interruption.
- Contracts: outsource high-risk activities to specialists with strong SLAs and audit rights.
Clarify in writing who does what if the event occurs, and how you will validate performance.
Purchase insurance policies as a risk response option within your risk management plan
Work with a broker to match coverage to your real exposures and appetite. Review your footprint annually as it changes (e.g., new products, markets, or vendors).
Outsource high-risk activities to implement specialized risk treatment
Examples:
- Managed security service providers for 24/7 monitoring.
- Specialist logistics for cold chain or high-value shipments.
- External counsel for complex regulatory regimes.
Outsourcing reduces certain risks, but adds vendor risk — keep due diligence and monitoring tight.
✅ Risk Acceptance
Risk acceptance means you formally decide to tolerate a risk because the cost of mitigation is higher than the potential impact if it occurs.
Example: a small business may accept the risk of a 30-minute website outage rather than pay for a full secondary data center.
Document accepted risks in the register so leadership knows what has been consciously left “as is.”
Risk Management Process #7–8: Monitor, Review, and Adapt
TL;DR
👉🏻 Build a monitoring system with KRIs and dashboards.
👉🏻 Run periodic risk reviews to re-score and reprioritize.
👉🏻 Keep responses current as your environment changes.
Establish risk monitoring with KRIs (for effective risk management)
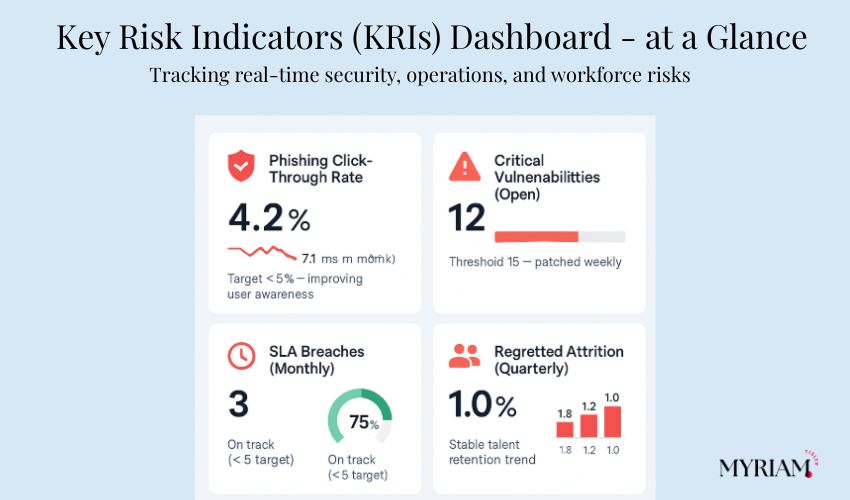
KRIs turn risk from opinion to evidence. Pick a handful you can measure without drama, and then commit to reviewing them on a schedule.
KRIs are early warning signals. Choose a few that matter:
- Security: patch age, number of open critical vulnerabilities, and phishing click-through rates.
- Operations: SLA breaches, defect leakage, backlog growth, capacity vs. demand.
- People: regretted attrition, and vacancy time in critical roles.
- Customer: complaints per 1,000 orders, churn in at-risk segments.
Automate collection where possible and show trends, not just snapshots.
Set up KRIs and thresholds inside your risk management plan
For each KRI:
- Define the metric and data source.
- Set thresholds (normal/alert/action).
- Name an owner and review cadence.
- Link the KRI to registered risks so action is explicit.
Use dashboards to track risk response trends and highlight common risk patterns
Keep dashboards simple:
- One page per audience.
- Clear red/amber/green indicators.
- Short commentary on what changed and what happens next.
- Alerts when thresholds are breached, sent to the right people.
Run regular risk reviews and refresh risk management steps
Book it in the calendar. A disciplined review prevents drift.
- Re-score top risks.
- Close items that are genuinely controlled.
- Add new risks from incidents, audits, and market shifts.
- Update owners and deadlines.
Reassess types of risks and update owners to manage risk
Sanity-check the mix of risks on your register:
- Are you overweight in one area (e.g., IT) and blind elsewhere (e.g., suppliers)?
- Do owners have capacity? If not, reassign.
- Are control effectiveness ratings still true?
Update risk management strategies and align risk response to changes
When the environment shifts, so should your response:
- New laws, technology, suppliers, or geographies may change exposure.
- Retire controls that no longer move the needle.
- Fund the ones that do.
Real-world Examples of Risk Management Strategies (What to Implement Now)
Let’s look at three real-world case studies: in supply chain, cybersecurity, and finance, to see how different risk management strategies work in practice.
Case study 1: supply chain risk management process and mitigation strategies
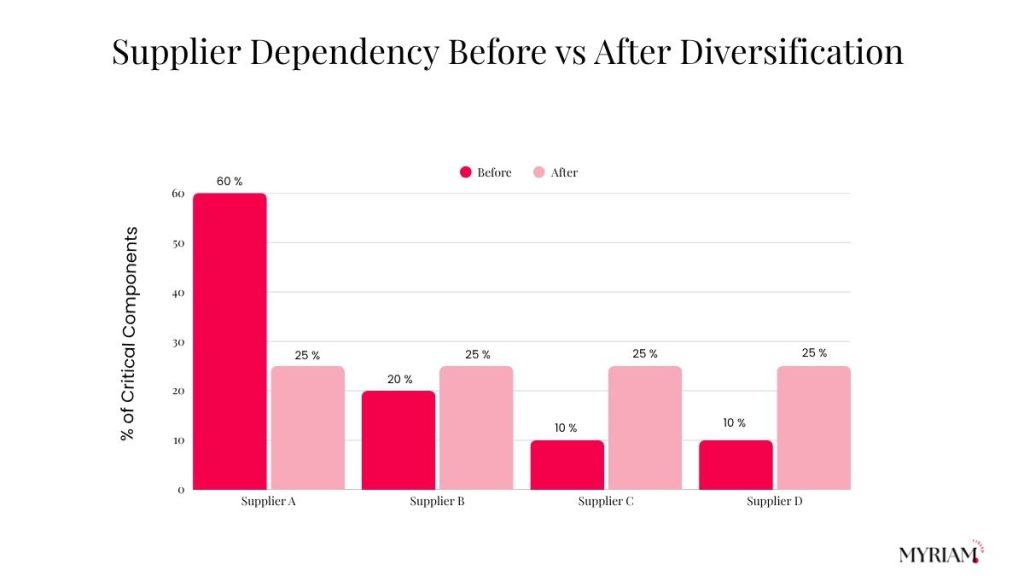
A global manufacturer reduced disruption risk by:
- Diversifying suppliers so no single vendor holds more than 20% of a critical component.
- Adding buffer stock for long-lead items.
- Real-time monitoring of inventory, transit milestones, and supplier health.
When an unexpected port strike hit, they switched suppliers and moved production without halting fulfillment.
Real-time monitoring, contingency playbooks, and risk response triggers
The company built playbooks for common disruption scenarios:
- Which alternate suppliers to call.
- How to resequence production lines.
- What to tell customers and when.
Triggers (e.g., missed milestones, quality dips) automatically launched the correct playbook.
Case study 2: Cyber risk management with controls that implement risk mitigation
A financial services firm cut breach exposure by pairing technology with behavior change:
- MFA everywhere, strong encryption, and least-privilege access.
- Employee training with phishing simulations and rapid feedback.
- Routine vulnerability scans and external pen tests.
- Practiced incident response with named roles and timelines.
The result: fewer successful phishing attempts, faster detection, and lower recovery time.
Employee training, awareness, and an effective risk management culture
Training wasn’t a one-off. The firm ran short, frequent refreshers, and tied completion to access privileges. Managers saw KRI dashboards so they could coach teams quickly.
Case study 3: Financial Risk Controls and Risk Treatment Choices
A multinational facing currency and rate volatility:
- Hedged exposures with forwards, options, and swaps.
- Diversified investments across assets and regions.
- Set limits by counterparty, sector, and country, with stress testing.
Volatility didn’t disappear, but earnings became more predictable, and capital planning improved.
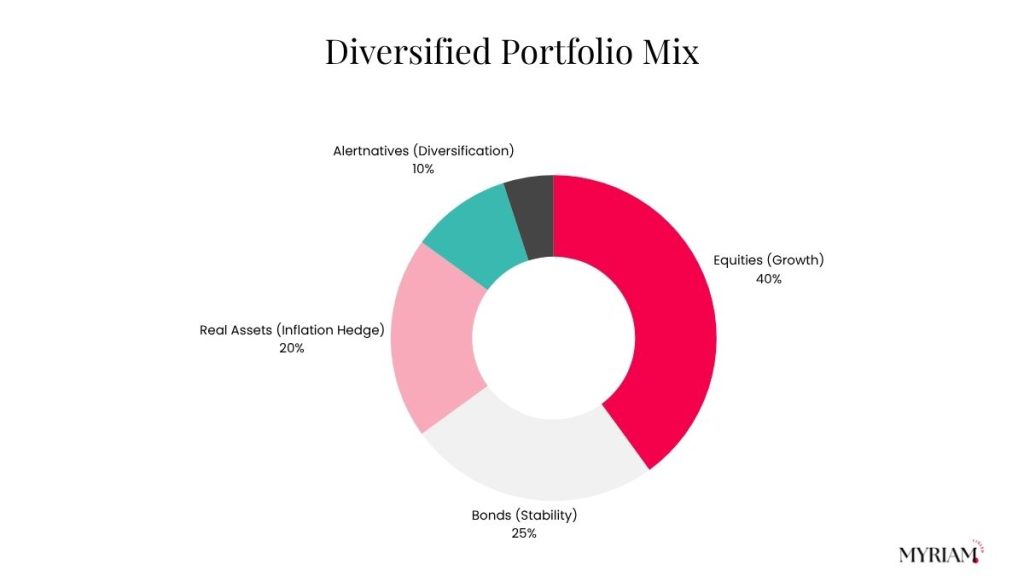
Diversified portfolio as a risk response within the risk management plan
The plan documented target allocations, rebalancing rules, and exception handling, so that decisions were made faster and less emotionally charged during market swings.
Asset Class | Target Allocation | Example Instruments |
|---|---|---|
Equities | 40% | Global stocks, ETFs |
Fixed Income | 25% | Bonds, treasuries, corporate debt |
Alternatives | 20% | Real estate, private equity, commodities |
Cash & Liquidity | 10% | Money market funds, short-term deposits |
Geographic Diversification | 5% (overlay) | Emerging vs developed markets |
Best Practices for Effective Risk Management (Make it Stick)
TL;DR
🧭 Build a risk-aware culture.
🤝 Coordinate across departments.
⚡ Improve continuously with lessons learned.
Foster a risk-aware culture to manage risk every day
Make it easy to raise a hand when something looks off.
- Praise early reporting.
- Keep channels open (anonymous if needed).
- Close the loop so people see that speaking up leads to action.
Establish clear reporting channels for common risk escalation
Offer simple routes: a Slack/Teams channel, a short form, or a named coordinator. Publish how to escalate and what happens next.
Collaborate across departments to coordinate risk response
Silos create blind spots. Use cross-functional reviews and shared dashboards so that finance, ops, IT, and legal are solving the same problems with the same information.
Continuously improve the risk management process with lessons learned
After incidents or near-misses:
- Capture what failed and what worked.
- Update playbooks and controls accordingly.
- Share the lesson in one page or less — fast to read, easy to apply.
Incorporate lessons learned into the risk management plan and controls
Incorporate improvements into the plan, and assign an owner and a target completion date. Re-score the affected risks to confirm that the change made a difference.
⚡ Lessons Learned Example:
A global SaaS firm cut downtime by 40% after a security incident revealed weak escalation paths. Their fix? They built a one-page playbook, set 15-minute response KPIs, and assigned clear owners. The next outage was contained in under an hour: proof that embedding lessons learned directly into the risk management plan makes strategies more resilient.
Leverage technology and data analytics in risk management activities
Use tools that match your size and maturity:
- Start with spreadsheets and simple dashboards.
- Add ticketing, asset inventories, and SIEM as you grow.
- Automate alerts where data quality is strong.
The aim isn’t fancy software. It’s faster detection, clearer decisions, and cleaner execution.
Maturity | Core tools | When to add next |
|---|---|---|
Starter | Excel/Google Sheets, Google Data Studio/Looker Studio, Slack/Teams alerts | When your register grows past ~30 risks or updates are missed |
Growing | Jira/ServiceNow (tickets), Asset inventory (Lansweeper), SIEM (Microsoft Sentinel) | When you need audit trails, auto-alerts, and ownership |
Advanced | Data warehouse + BI (BigQuery/Redshift + Power BI), SOAR automation, Vendor risk platforms | When you’re correlating KRIs across teams and automating playbooks |
Developing a risk management strategy with KPIs and owner accountability
A risk management strategy is only effective if you can track progress and know who’s responsible. That’s why every plan needs both KPIs and clear ownership.
1. Define measurable KPIs
Choose indicators that show whether your mitigation strategies are working. For example:
- % of types of risks with assigned controls in the risk register
- Time taken to respond to a typical risk response
- Number of incidents reduced after new risk mitigation measures
- Compliance with scheduled risk management steps (like quarterly reviews)
2. Assign accountable owners
Every risk in your risk management process should have a named owner. Ownership isn’t about doing all the work — it’s about ensuring the risk is monitored, responses are triggered, and updates are logged.
3. Review and report regularly
Make KPIs visible in dashboards or reports. When owners know their metrics are being reviewed, they’re more likely to implement changes quickly and embed effective risk management into daily routines.
By combining KPIs + accountability, you move from theory to practice. Teams don’t just “have a plan” — they know how to measure success, prove it, and continuously manage risk more effectively.
Provide ongoing training and support for effective risk decisions
Training sticks when it’s:
- Brief and regular.
- Tailored to the role (frontline vs. leadership).
- Tied to real scenarios and clear actions.
- Give access to risk management experts.
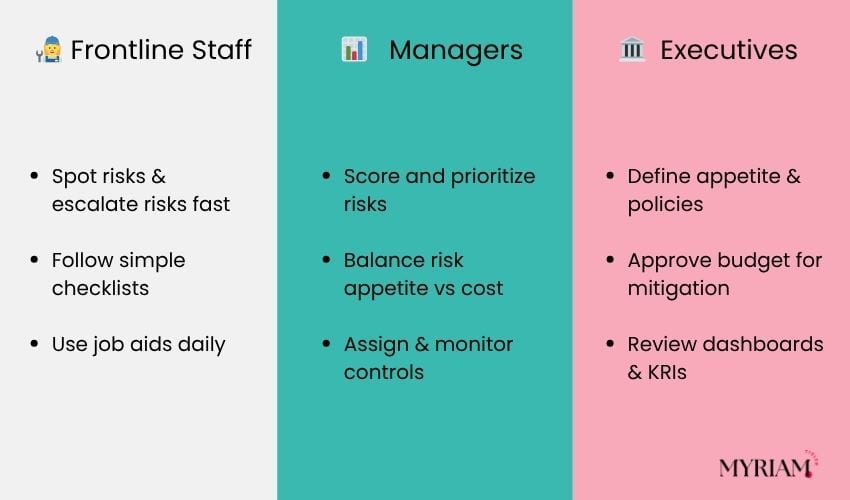
Tailor training by role to implement risk controls consistently
- Frontline: spotting issues, how to escalate, follow the checklist.
- Managers: scoring, trade-offs against appetite, resourcing controls.
- Executives: appetite setting, funding priorities, reading KRI trends.
Role | Focus Area | Training Topics & Format |
|---|---|---|
Frontline | Spotting issues, escalation, checklists | Appetite setting, funding, and KRI interpretation |
Managers | Scoring & trade-offs, resource allocation | Risk assessment scoring workshops, balancing appetite vs. cost, assigning controls |
Executives | Learn to identify risks in daily work, follow escalation paths, use job aids, and checklists | Define risk appetite, approve budgets for controls, review dashboards & KRI trends |
Protect Your Business with Proven Risk Management Strategies (Align Your Risk Management Plan)
Effective risk management isn’t a binder on a shelf. It’s a rhythm:
Identify and assess.
Prioritize and treat.
Monitor and review.
Improve after every incident.
Do that consistently and you’ll protect revenue, reputation, and people — and you’ll make better, faster decisions when things change.
Why listen here?
Having started my project management career in financial services, risk management was intertwined into every deliverable. Over the years, I’ve applied the same methods across sectors — from global corporates to creative industries — and clients kept saying the same thing: risk workshops gave them clarity and confidence because we were proactive, not reactive.
Practical next step:
Pick one high-impact risk. Assign an owner. Add one control this week.
That single move builds momentum, confidence, and proof that your strategy works.
What’s the first risk you’ll address?
Start by reviewing your current risk management practices and identifying areas for improvement. Engage your team in discussions about potential risks and brainstorm strategies to mitigate them. Remember, proactive risk management is key to building a resilient and successful business.
FAQ: Common Questions About Risk Management Strategies
Q1. What’s the difference between risk mitigation and risk acceptance?
Risk mitigation means putting controls in place to reduce the likelihood or impact of a risk. Think MFA to cut cyber exposure or backup suppliers to mitigate supply chain delays. Risk acceptance, on the other hand, is choosing to live with the risk because it’s low-cost, low-likelihood, or not worth fixing. The key is being intentional — don’t “ignore” risks, decide consciously which ones to accept.
Q2. How often should a risk register be updated?
A risk register should be treated like a living document. At a minimum, review it quarterly. In fast-moving industries, monthly updates are best. Anytime there’s a major change: new regulation, market disruption, or an internal incident, update your register right away. The fresher it is, the more useful it becomes for decision-making.
Q3. What is risk appetite, and why does it matter?
Risk appetite is your organization’s comfort level with uncertainty. For example, a fintech startup might accept higher cyber risk for faster growth, while a healthcare provider has zero tolerance due to compliance requirements. Getting clarity on appetite helps teams decide whether to avoid, mitigate, transfer, or accept a risk. Without it, risk decisions become inconsistent.
Q4. When should you transfer a risk to a third party?
Risk transfer works when the cost of controls outweighs the exposure. Classic examples: buying insurance for natural disasters or outsourcing IT security to a specialist. The golden rule — transfer high-cost, low-frequency risks to providers who are better equipped to absorb them.
Q5. What’s a simple way to score risks in a small business?
Keep it lightweight. Use a 1–5 scale for likelihood and a 1–5 scale for impact. Plot them on a matrix and focus on anything that lands in the “high/high” box. No need for complicated models — even a spreadsheet works. What matters most is consistency in how you score and review.
Q6. Can you combine qualitative and quantitative risk assessments?
Yes, and it’s often the smartest move. Qualitative scoring (low/medium/high) helps you get started quickly and align teams. Quantitative analysis (e.g, financial impact in dollars, downtime in hours, etc.) makes the case for funding and prioritization. The best risk management strategies use both, scaling detail to the size of the decision.
An example of a risk management strategy is building a risk register, prioritizing threats, and applying mitigation strategies that cut exposure before problems escalate. This post outlines ten practical approaches — from running a structured risk assessment to setting KPIs and creating response playbooks. You’ll also see real-world examples in supply chain, cybersecurity, and financial risk management. By the end, you’ll know how to implement a risk management plan, monitor it with KRIs, and adapt it over time so your business can stay resilient against different types of risks.