According to PMI’s Pulse of the Profession report, 67% of projects fail to meet at least one of their goals, and most of those failures come from unmanaged risks, not bad luck. The good news: you can fix that today. A simple {{risk management plan}} turns those “out of nowhere” problems into checklists you control.
Why it matters: Risks are unavoidable, but being blindsided isn’t. Whether you’re managing a product launch, an event, or an IT rollout, having a plan in place is what separates smooth delivery from expensive surprises.
What you’ll learn: In this guide, you’ll see a risk management plan example to see how to identify project risks, score them, write a practical risk mitigation plan, and keep a living risk register that your team will actually use. I’ll also share real-world examples and a quick-start version you can create in a single day.

A risk management plan explains how you identify, score, and treat project risks using a simple plan template with a risk register, a risk assessment matrix, and weekly risk monitoring. This guide shows you the exact steps, plus examples, so you can build a plan your team will follow.
How to Create a Risk Management Plan in One Day (Quick Start)
When I worked on a global call center transformation project in 2016, our initial risk register had 32 items — yet 70% of them never moved. What changed outcomes was introducing a simple ‘top 5 risks’ rule, which kept leaders focused on what truly mattered week to week.
Short on time? Do this today.
- List 10 potential risk items across scope, budget, timeline, people, tech, and compliance.
- Score each (1–5) for likelihood and impact. Multiply for a risk score.
- Top 5 only: draft a one-line {{risk mitigation}} action, an owner, and a due date.
- Create a basic risk register (ID, title, category, owner, likelihood, impact, score, action, next review).
- Book a 30-minute review every Friday. That’s your {{risk monitoring}} cadence.
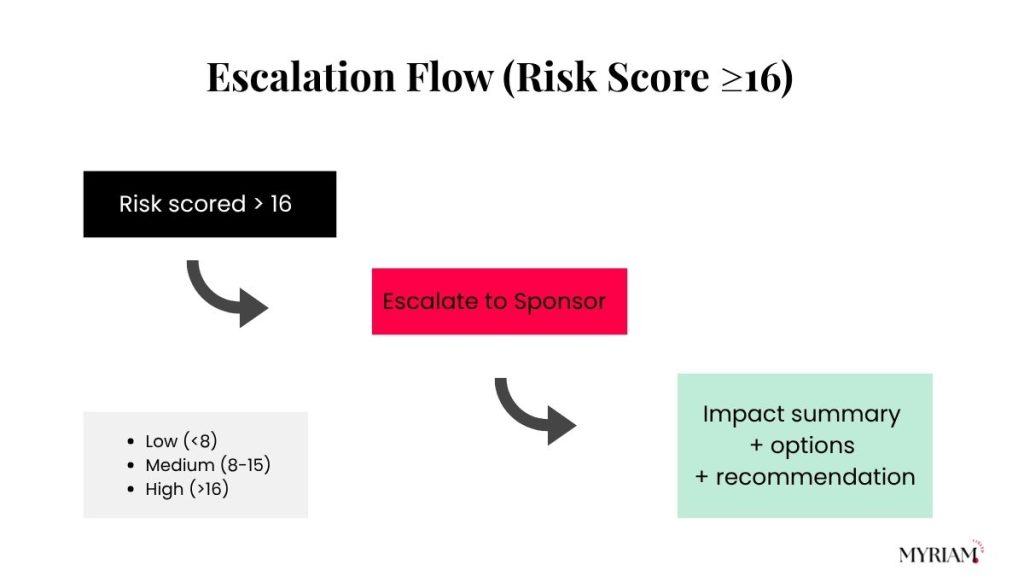
- Escalation rule: score ≥ 16? Ping the sponsor within 24 hours.
See the escalation flow below, so your team knows when a high-score risk (≥16) goes straight to the sponsor.
Risk Management Plan Template: A Step-by-Step Guide to Create a Risk Management Plan

The plan only works if it’s simple enough to use on a weekly basis.
Step 1: Risk identification — list every potential risk
Run a 20-minute workshop. Prompt for budget, scope, timeline, resourcing, data, vendors, compliance, UX, rollout. Capture each item in the risk register with a short description.
Step 2: Assess & prioritize project risks – scoring for an effective risk management plan
Use a 1–5 scale for likelihood and impact. Multiply to get a score. Work the top five first. Low scores can wait.
Step 3: Risk mitigation strategies – how to develop a risk response that works

Pick one per risk: avoid (change scope), reduce (controls/tests), transfer (contract/insurance), accept (watch with a trigger): record owner and date. Assign risk owners & RACI for effective risk management.
Make one person accountable (A). Limit the “consult” and “inform” lists so actions don’t stall.
Establish contingency plans
Pre-write the first move if the risk fires, including comms, rollback steps, and a timebox for decision.
Build your risk register structure

Define thresholds & triggers for risk monitoring
Write clear rules: score ≥16 → sponsor in 24h, two missed sprints → scope review, SLA breach → vendor switch plan. Triggers prevent slow-burning risks.
Step 4: Monitor and review project risks – set up ongoing risk monitoring
Run a weekly 15–30 minute review. Close completed actions, add new risks, re-score anything that is aging, and refresh the top-5 list.
Escalation routes and owners for high-severity risks
Document who escalates, to whom, in what channel, and within what time. Include an impact summary, options, and a clear recommendation in every escalation.
References: For standards and terminology that underpin monitoring and escalation, see the PMI guide Risk Management in Portfolios, Programs, and Projects, ISO 31000 Risk Management guidelines, the COSO ERM framework, and ISACA’s Risk IT. For a public explainer on the {{risk assessment matrix}} used in prioritization, Thomson Reuters’ overview is clear and accessible.
— PMI: Risk Management in Portfolios, Programs, and Projects Project Management Institute
— ISO 31000:2018 — Risk management — Guidelines ISO
— COSO: Enterprise Risk Management (ERM) Framework COSO
— ISACA: IT Risk Resources (Risk IT) ISACA
— Thomson Reuters: What is a risk assessment matrix? Thomson Reuters Legal
Risk Assessment Matrix: Prioritizing Project Risks for Project Risk Management
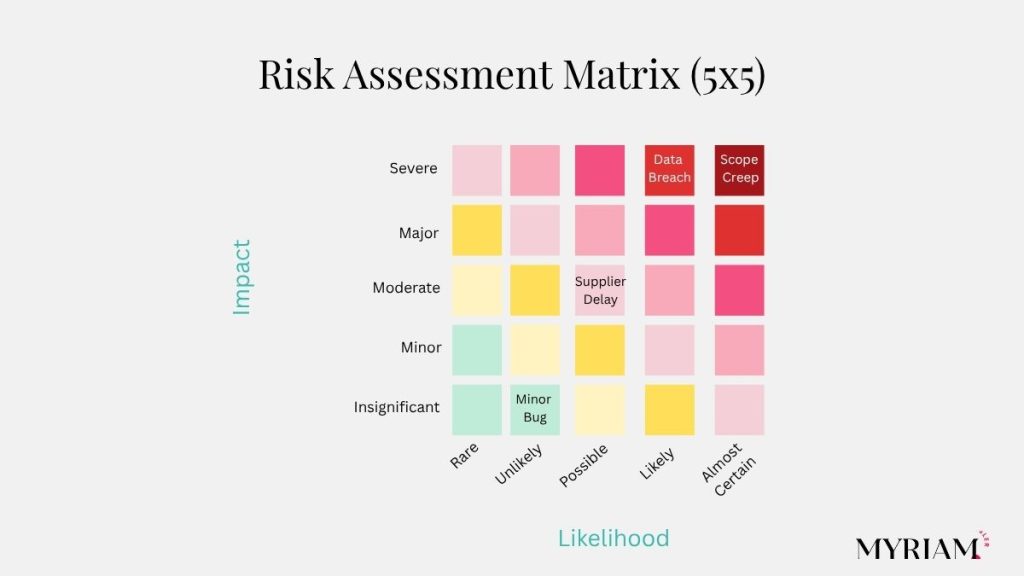
Use this grid to align stakeholders quickly on where to act first.
What is a risk assessment matrix?
It’s a 5×5 grid of likelihood vs impact that shows where to act first. Plot each risk, then attack the top-right quadrant: impact to focus effort.
Creating a matrix: the key step in the risk management process
Define scales, plot risks, label the immediate action zone, and add the grid to stand-ups and sponsor decks. Re-plot after major changes.
Address high-priority items with a risk mitigation plan
Give each red-zone risk one owner, one action, and one deadline. Track progress in the risk register.
Ongoing risk monitoring & matrix updates
Re-plot every sprint/milestone. If a risk moves up or right, escalate. If it moves down or to the left, reduce attention and free up capacity.
Benefits of Using a Risk Assessment Matrix
A visual matrix improves prioritization (see the hot spots fast), communication (stakeholders align in minutes), and decision-making (resources shift to the biggest impact with less debate).
#4: Build and Maintain Your Risk Register
If it isn’t in the register, it won’t get managed.
Fields to include
Capture the basics, plus the residual risk after treatment, so that leaders can see the remaining exposure. Keep entries short and actionable.
Track assumptions and dependencies in the register
List what must remain true and what it depends on. When a dependency slips, re-score linked risks.
Capture residual risk after treatment
Record the “after controls” score to show what’s left. This helps justify additional funding or scope trade-offs.
Link risks to the issue log and change control
When a risk materializes, convert it into an issue and, if the scope shifts, trigger change control with an impact, options, and a decision needed.
Update cadence, ownership, and “Top-10” review
Publish a “Top-10 risks” snapshot weekly. If actions stall for two cycles, rotate ownership or escalate.
Weekly aging risks review and next-review dates
Flag items untouched for 14+ days. Add a next-review date to every entry so nothing goes stale.
Types of Project Risks and How to Address Them
Different risks, same playbook — identify, score, treat, monitor.
Risk Type | Typical Risks | How to Treat / Control |
|---|---|---|
Financial | Costs overruns, funding delays | Cost overruns, funding delays |
Operational | Resource gaps, bottlenecks, quality slippage | Capacity planning, SOPs, QA checks |
Legal / Compliance | Regulatory breach, licensing, data issues | Star-gate legal reviews, audit trails |
Strategic | Market shifts, priority changes | Scenario planning, agile reviews, stop/go gates |
Technology / Cyber | Data breach, weak IAM, fragile integration | MFA, encryption, disaster recovery, pen tests |
Supply Chain | Vendor delays, SLA branches | Dual sourcing, exit clauses, continuous monitoring |
Financial Risks
- Typical: cost overrun, funding delay, FX change.
- Treat: tighter estimates, change budget gates, contingency (5–15%).
- Control: monthly variance reviews.
Contingency Planning
Allocate a portion of the budget for unknowns, sized by risk scores and historical data. 5–15% is common, scaled to complexity.
Operational Risks
- Typical: resource gaps, process bottlenecks, quality decline.
- Treat: resourcing plan, WIP limits, QA checklists, runbooks.
Process Optimization
Map workflows, remove bottlenecks, and define handoff SLAs. Use lean/Six Sigma tools to cut waste and stabilize quality.
Legal and Compliance Risks
- Typical: regulatory breach, licensing, data residency.
- Treat: legal reviews by stage, DPA updates, audit trails, and training.
Compliance Monitoring
Schedule audits and release checklists. Keep evidence folders current to reduce remediation later.
Strategic Risks
As Dr. David Hillson, known as the “Risk Doctor,” put it: “Risk is uncertainty that matters” (Hillson, PMI Conference, 2019). Source link.
- Typical: priority shifts, market changes.
- Treat: quarterly scope check, scenario planning, and option “kill switches.”
Agile Approaches
Short cycles and frequent feedback let you pivot fast. Use sprint reviews to re-score risks and adjust scope. Agile risk practices can be built directly into each sprint, so risks are logged, assessed, and closed within the same cycle. Both ISACA’s guidance on Agile risk management and Invensis Learning’s overview show how embedding risk reviews into daily stand-ups keeps projects adaptable without losing control.
Technology & Cyber risks
Typical risks include data breaches, weak IAM setups, and fragile integrations with external systems. Strong controls, such as multi-factor authentication, end-to-end encryption, and disaster recovery planning, are non-negotiable. Regular penetration tests and secure integration checkpoints are also recommended, as highlighted in BitSight’s definition of third-party cyber risk.
Third-party & supply chain risks
Vendors often introduce hidden vulnerabilities: from missed SLAs to compromised software. To reduce exposure, build dual sourcing into contracts, apply clear exit clauses, and continuously monitor suppliers. The CyberSaint supply chain risk guide and CISA’s ICT supply chain framework both stress that third-party cyber risk management is now a board-level priority, not an optional extra.
Risk Management Strategies for Financial, Operational, Legal, and Strategic Risks

Strategy only matters if it’s easy to execute every week. If you’d like a complete risk management strategy example that shows how to avoid, reduce, transfer, accept, and use contingency tactics together, this breakdown walks through a full strategy in context.
Financial risk management strategies (e.g., budgeting, cost control)
- Budget baselines, PO thresholds, contingency pool, and monthly CFO review.
- Monitoring: a simple burn-down chart in your dashboard.
Effective financial risk management starts with a realistic budget that includes labor, materials, and overhead, and gets reviewed regularly. Add controls like PO thresholds and CFO sign-off to prevent overspending. Set aside a contingency fund (5–15% of the budget, scaled to project complexity) for unexpected expenses. Visual tools such as a budget vs. actual chart or burn-down graph help teams spot issues early and keep costs on track.
Monitoring and reporting financial risks

Track actuals vs budget, investigate variances, and publish a simple burn-down chart for transparency.
Operational risk management strategies (e.g., resource planning, scheduling)
- Clear RACI, Kanban/Gantt visibility, capacity planning, SOPs for handoffs.
- Contingency: named backups for critical roles.
Operational risks often show up as delays, missed handoffs, or quality drift. To reduce them, map out roles with a clear RACI, and make schedules visible in Kanban boards or Gantt charts. Build in capacity checks so workloads stay realistic, and document handoff steps with SOPs. Always prepare contingencies for key roles — name backups in advance and pre-approve options like overtime or contractors so the project doesn’t stall when someone is out.
Contingency planning for operational risks
Name backups for critical roles and pre-approve overtime or contractors for spikes.
Legal and compliance risk management strategies (e.g., due diligence, contracts)
- Stage-gate reviews with Legal/InfoSec, evidence folders, and training logs.
- Monitoring: audit checklist per release.
Legal and compliance risks are expensive if they slip through late. Run due diligence before work begins, then bake checks into every stage gate: involve Legal and InfoSec, and keep evidence folders audit-ready. Contracts should spell out roles, deliverables, and compliance obligations clearly, with all parties signed off. Finally, add compliance monitoring to the delivery cycle itself: use an audit checklist per release, log training completion, and fix gaps immediately instead of waiting for regulators to find them.
Monitoring and auditing for legal and compliance risks
Use audit checklists per release and remediate gaps with owners and deadlines.
Strategic risk management strategies (e.g., market research, scenario planning)
- Quarterly OKR/roadmap alignment, “stop/go” criteria, and option analysis.
- Continuous assessment: re-score if leadership priorities change.
Strategic risks pose a threat to long-term viability when markets shift or priorities change. Stay ahead by running quarterly OKR and roadmap alignment sessions, backed by current market research and competitor tracking. Use scenario planning with “stop/go” criteria to pivot or pause projects before they exceed budget. Agile approaches help here: short sprints, regular reviews, and continuous feedback loops let you re-score risks fast and adjust direction before issues escalate. Together, these practices keep projects aligned with organizational goals while giving you the flexibility to adapt.
Continuous strategic risk assessment
Re-score when priorities shift or assumptions break. Document decisions.
Choosing risk management tools & templates
- Start with a spreadsheet. If complexity grows, move to Smartsheet/Jira/Asana.
- Keep the plan template short. A plan people read beats a perfect plan no one opens.
Best practices of the best risk management plans
- One-page summary, live risk register, weekly cadence, clear triggers, visible owners.
What is Project Risk Management? Process, Steps, and Benefits
Plain English: fewer surprises, better decisions.
Definition & why effective risk management matters
In simple terms, project risk management is the repeatable process of spotting issues early, scoring them, and deciding how to respond before they derail scope, budget, or timelines.
Identify, score, treat, and track risks so you can hit scope, budget, and time with fewer escalations and more predictable delivery.
What’s included in a risk management plan?
One mistake I see often is teams treating the risk register as a one-time document. The pitfall: it becomes outdated in weeks. The fix is to treat it like a product: review weekly, close items fast, and refresh as priorities shift.
A comprehensive risk management plan should include the following key components:
Risk identification techniques
Brainstorming, pre-mortems, checklists, and expert interviews to surface unknowns.
The goal isn’t just to make a long list: it’s to gather risks from every angle. Involve diverse stakeholders (team, SMEs, customers, vendors) so you capture blind spots early. A structured session, plus a simple checklist, will usually surface 80% of the risks that matter.
Risk Assessment and Prioritization
Likelihood × impact scoring, with a visual matrix to focus effort.
Give each risk a likelihood (1–5) and an impact (1–5), then multiply for a score. Focus on the high scorers — those are the ones most likely to derail your project and deserve detailed response plans first.
Risk | Probability | Impact | Risk Level | Owner | Mitigation Plan |
|---|---|---|---|---|---|
Adverse weather | 50% | High | High | Project Manager | Choose indoor venue |
Transportation for participants is delayed | 10% | Low | Low | Event Coordinator | Accept |
Catering costs $1,000 more than expected | 30% | Medium | Medium | Event Coordinator | Avoid: Find caterer that can guarantee a fixed price up front |
Activities may lead to injury | 10% | Medium | Medium | Legal Associate | Transfer: Require liability waivers |
Activities may lead to injury 10% Medium Medium Legal associate Transfer: Require liability waivers
Build a risk mitigation plan with owners, actions, and timelines
Select ‘avoid’, ‘reduce’, ‘transfer’, or ‘accept’, document the action, and set a date.
Set up risk monitoring cadence & reporting
Weekly reviews, monthly sponsor summaries, and an always-on dashboard.
Maintain a living risk register
Update entries as facts change, add new risks quickly, and close obsolete ones. The register is a product, not a static document.
Governance & escalation paths (triggers/thresholds)
Governance & escalation paths
See the escalation flow visual above for an overview of how high-severity risks are routed, with clear thresholds and ownership.
Define who decides what, and when. Use thresholds (e.g., score ≥16, missed milestone, vendor breach) to trigger fast decisions.
Further Reading and Resources
PMI Practice Standard for Risk Management, ISO 31000, COSO ERM, and ISACA Risk IT are solid baselines. Use them to refine your process without bloating it.
Risk Management Plan Examples: Financial Services, Media, and IT
Same mechanics, different realities: here’s how it plays out.
Example 1: Financial services risk management plan example

Situation: A financial services client faced escalating regulatory risks after a sudden FCA mandate in 2017. Action: I helped design a compliance-driven risk register with legal checkpoints at each stage of the project. Result: The remediation program cleared audit review in 10 weeks, cutting potential fines by 40%.
Financial services projects face intense scrutiny due to regulatory, data, and compliance requirements. Risks often come from changing regulations, customer data handling, and remediation programs.
Regulatory & compliance risks
Add FCA/PCI checkpoints and evidence to the risk register at each stage of the process.
Data security risks
MFA, encryption at rest/in transit, quarterly pen tests, named data owners.
Stakeholder alignment risks
Stage-gate sign-offs and weekly risk reviews keep interpretations aligned.
📌 Pro tip: Review risks monthly, not quarterly. Regulatory projects change fast, and risk monitoring should match that pace.
Example 2: Media & events risk management plan example

Events and media projects carry operational and reputational risks — from last-minute cancellations to negative press.
Event disruption risks
Backup venues, flexible cancellation clauses, contingency funds.
Supplier and partner risks
Dual-source AV/catering/print, keep backup contacts in the register.
Reputational risks
In media-heavy projects, reputational harm can spread quickly. Create a crisis communications plan, designate media spokespeople, and rehearse responses. These strategies belong in your risk mitigation section so that the team knows exactly how to respond.
📌 Pro tip: Include reputation risks in your risk management tools dashboards — many teams forget to track these alongside operational ones.
Example 3: IT project risk management plan example
IT projects come with their own unique set of risks, such as data security concerns, compatibility issues, and fast technological changes. When developing a risk management plan for an IT project, consider the following risks:
Cybersecurity risks
Harden IAM, patching, SIEM alerts, and incident runbooks.
Integration risks
Early POCs and technical due diligence before contracts.
Scope creep
Strict change control, definition of done, WIP limits.
IT projects are magnets for new “must-have” features. If you don’t set boundaries, timelines, and budgets, they slip. Control scope creep by enforcing change approval gates, agreeing on a clear “definition of done,” and limiting work in progress so the team finishes priorities before starting extras.
Example 4: Healthcare risk management plan example (industry illustration)

Healthcare projects deal with strict compliance and patient safety risks, which makes {{effective risk management}} non-negotiable.
Clinical compliance risks
HIPAA/GDPR evidence trails, consent checks, and audit logs.
Patient safety risks
Track high-impact items with clear escalation triggers.
Operational continuity risks
Staffing plans, equipment spares, and daily risk monitoring huddles.
Frequently Asked Questions about Risk Management Plans
What are the 5 risk management strategies?
Avoid, Reduce, Transfer, Accept, Contingency. If you want a practical example of a risk strategy that applies these five approaches to real project risks, this guide walks through them step by step.
5 risk management plan examples
Strategy | What it Means | When to Use | Example |
|---|---|---|---|
| Avoid | Eliminate the risk entirely by changing scope or approach. | High-impact, non-negotiable risks. | Cancel a feature that would break compliance. |
| Reduce | Put controls in place to lower likelihood or impact. | Common operational or financial risks. | Add QA testing or stronger vendor SLAs. |
| Transfer | Shift responsibility to another party. | Risks that can be insured or outsourced. | Buy cyber insurance or outsource payroll. |
| Accept | Live with the risk and monitor it over time. | Low-likelihood or low-impact risks. | Accept a minor delay in non-critical reporting. |
| Contingency | Prepare a backup plan if the risk occurs. | Medium/high risks that can’t be avoided. | Identify alternate suppliers or reserve extra funds. |
Finance, Media/Events, IT, Healthcare (generic), plus one from your niche.
What’s the difference between a risk register and an issue log?
Register = potential risks. Issue log = events that already happened.
Where can I find a sample risk management plan?
A: This guide includes risk management plan examples from finance, media, IT, and healthcare — all serve as sample risk management plans you can adapt.
Equip Your Project for Success with a Successful Risk Management Plan
You’ve seen how a {{risk management plan}} isn’t just paperwork — it’s the difference between reacting to chaos and leading with confidence. The key insight? Keep your plan simple, up-to-date, and reviewed regularly.
Are You Ready to Tackle Risks Head-On?
The next step is yours. Start by setting up a risk register you’ll actually update, share it with your team, and run that first 15-minute review. From there, risks stop being surprises and become decisions you control.
Want a shortcut? [Download the editable risk management plan template] (insert link to your lead magnet). Use it as your baseline and adapt it to your specific industry, such as financial services, media, IT, healthcare, or your own niche.
Don’t wait until the next issue blindsides you. A successful risk management plan is built before the storm hits. So here’s the question to leave you with: what’s the first risk you’ll log and take off your shoulders today?
A risk management plan gives you a simple way to spot, score, and respond to project risks before they derail your goals. This guide explains how to create a risk management plan using a step-by-step template, from risk identification and scoring to writing a risk mitigation plan and keeping a live risk register. You’ll see examples from finance, media, IT, and healthcare so you can adapt the template to your industry. By the end, you’ll know how to monitor risks week to week, use risk management tools to stay on track, and build a successful risk management plan your team will actually follow.